- 17 Posts
- 54 Comments
Even in a galaxy far far away everything is still made in china


Edit: at least they didn’t use Phillips screws

 15·2 months ago
15·2 months agodeleted by creator

 10·2 months ago
10·2 months ago-
Joined: 9 years, 11 months ago
-
Last Seen: 19 secs ago
-
Uploaded: 137.847 TiB
-
Downloaded: 7.191 TiB
-
Ratio: 19.16
-
Required ratio: 0.50
-

 61·3 months ago
61·3 months agoAfaik profit is profit whether it’s from subsidies or sales. On top of that, the government gave them grants to develop said vaccines, so r&d was highly discounted… Production of most vaccines as way cheap compared to r&d, so I doubt there is ever any “selling for a loss”. Combine that with state mandates requiring kids to get vaccines before attending school (I’m not saying this is bad… Public health is a good thing), and you have a captive customer base.

 31·3 months ago
31·3 months agoAfaik profit is profit whether it’s from subsidies or sales. On top of that, the government gave them grants to develop said vaccines, so r&d was highly discounted… Production of most vaccines as way cheap compared to r&d, so I doubt there is ever any “selling for a loss”. Combine that with state mandates requiring kids to get vaccines before attending school (I’m not saying this is bad… Public health is a good thing), and you have a captive customer base.

 10·3 months ago
10·3 months agoA lot of Mr brain worms plans would seriously cut into the profits of major pharmaceuticals and agricultural behemoths that are major donors of Trump’s campaign. I can’t imagine them allowing trump to cut into their profits like that.

 5·3 months ago
5·3 months agoNgl I would smash. But not doordash…
I truly miss reveal codes. It was an amazing feature.
If I remember correctly, wordperfect was so prevalent that most of the key combos also worked in lotus word pro/ami pro and Microsoft word out of the box.

 24·4 months ago
24·4 months agoTrillian from hitchhikers guide to the galaxy. People see the book as satire but she really knew where her towel was.

 22·4 months ago
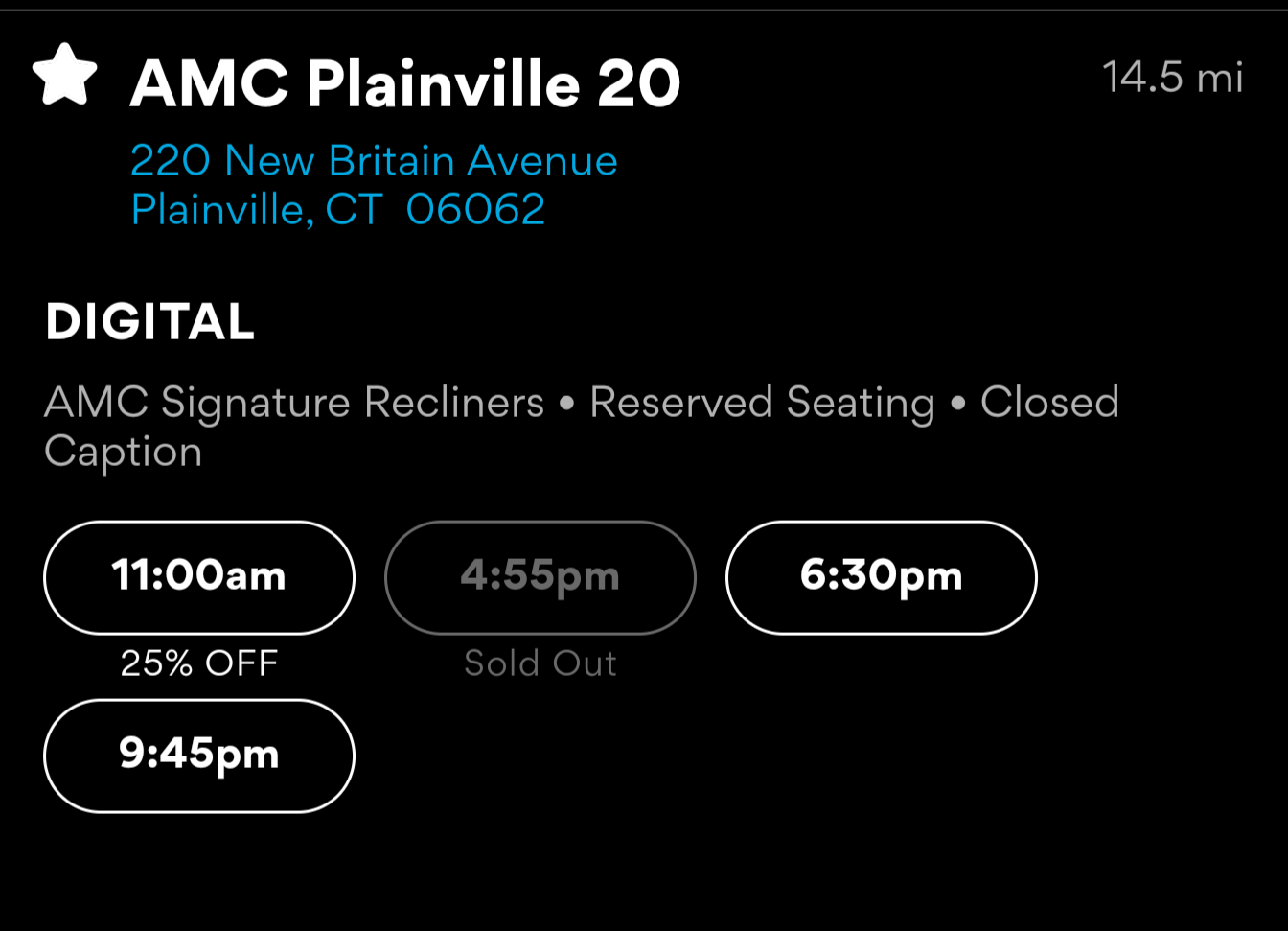
22·4 months agoI dont know how much I believe the theater. This is tomorrow in Connecticut. 4:55 sold out but all the other times have zero to 7 people. Yeah it’s a Sunday but I would t put it past thr gop to be artificially inflating box office receipts.


 4·4 months ago
4·4 months agoPolar bears and penguins lack the coordination for true kung fu mastery

 3·4 months ago
3·4 months agoEvery body (in the blue area) was kung-fu fighting. The parenthetical part was removed for rhyme scheme

 4·4 months ago
4·4 months agoNo. New Zealand is there. They were not kung-fu fighting. The places they were not kung-fu fight are cored white. It’s just unfortunate that it is also the background color

 2·4 months ago
2·4 months agoI actually use fish on my personal machine. But the servers I manage are pretty basic to save space and all just use stock bash.

 9·4 months ago
9·4 months agoNot a command as much as I press the up arrow a lot. I’m.pretty lazy and hitting the up arrow 12 times is easier then retyping a complex rsync command.

 8·5 months ago
8·5 months agoMy point (i.e. the “high hopes” part) is that this sounds legit and awesome. I do my best to be an optimist, but I have been burned way to many times to not concede that there may be ulterior motivation afoot.

 237·5 months ago
237·5 months agoI have high hopes but my logical side says they can just be pandering like any of the other politicians: they know people support it, they know it will fail. They look good for backing it even tho they aren’t worried about changing the status quo either
I’m not a big Morrissey fan, but he isn’t wrong herehttps://www.youtube.com/watch?v=TjPhzgxe3L0&t=26

 5·5 months ago
5·5 months agoMaybe it depends on the access point. When I turn it off on my router there are no beacons sent. Unless you specifically probe the ssid it doesn’t announce itself. BUT granted when you make a connection the ssid does show up during the handshake. If you were watching at the exact moment of connection then it would be detectable. I suppose they could use a mass deauther device and cause new connections and detect while that is happening but they they would need to triangulate the location of said ap… Again a lot of extra equipment.




I have a mikrotik at home and generally believe it to be a very solid product. A take aways from this hack:
mikrotik doesn’t bill themselves as “consumer grade”. It’s a huge learning curve to get started with them. There are graphical tools but it’s not much different then Cisco or juniper. You can put in bad or faulty configurations and the router will happily do the bad or faulty things you told it to.
It only effects routers that are severely misconfigured routers. You need specific services turned on, and have dns grossly misconfigured. Depending on your use case at home it is doubtful a hone user would do this. Also
the man thing I don’t like about my device is that the software isn’t open source. The hardware is quite well known tho and there are ports of *wrt and opensense that run on it , plus you probably could just run a Linux distro on it if you wanted. The bootloader isn’t locked down. It’s an arm64 computer with a lot of network ports.
That being said I really like the router itself. Performance is great, price is amazing. It does anything and everything I ask it to.